How to Create a MISP Feed from a Greynoise Trend
Introduction⌗
GreyNoise Trends are a feature offered on the platform which allows us to track IPs associated with a particular activity, exploit, or tool. These trends can also be benign or malicious. GreyNoise recently created a feature allowing users to utilize dynamic blocklists based on a particular trend.
For example, let’s say I wanted to track the latest exploit, CVE-2022-26138 (Hardcoded Confluence Password). As long GreyNoise has already created a tag for this CVE (which they have), I can access a URL that contains a list of IPs associated with this activity in a rolling 24-hour window.
These URLs containing the blocklists are meant to be utilized by firewalls which can proactively block these IPs in real-time, but MISP is also able to automate collections from remote URLs.
Getting Unique GreyNoise Trend URL⌗
Before we create our feed in MISP, we first need to retrieve the URL for the GreyNoise trend that also utilizes a unique key for our account (not the same as your API key).
Go to the GreyNoise Trends page and choose a tag that you are interested in, for this tutorial we’ll use the vulnerability we referenced before (CVE-2022-26138), which can be found here.
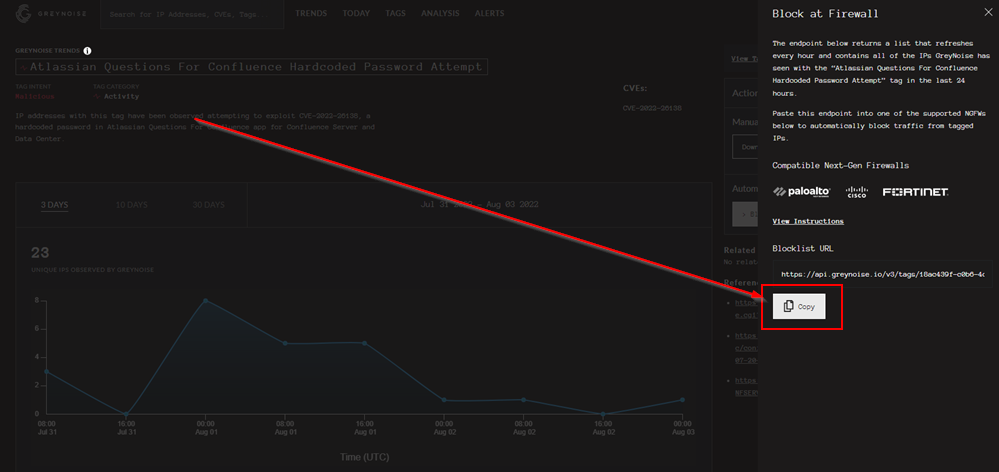
Once you’re on the page for the tag you just need to click “Block at Firewall”, and we’ll get a panel that contains our unique URL. Copy this URL because you will need it for the next part.
Creating the Feed in MISP⌗
First, we’re going to log into MISP and go to create a new feed; Sync Actions -> List Feeds -> Add Feed.
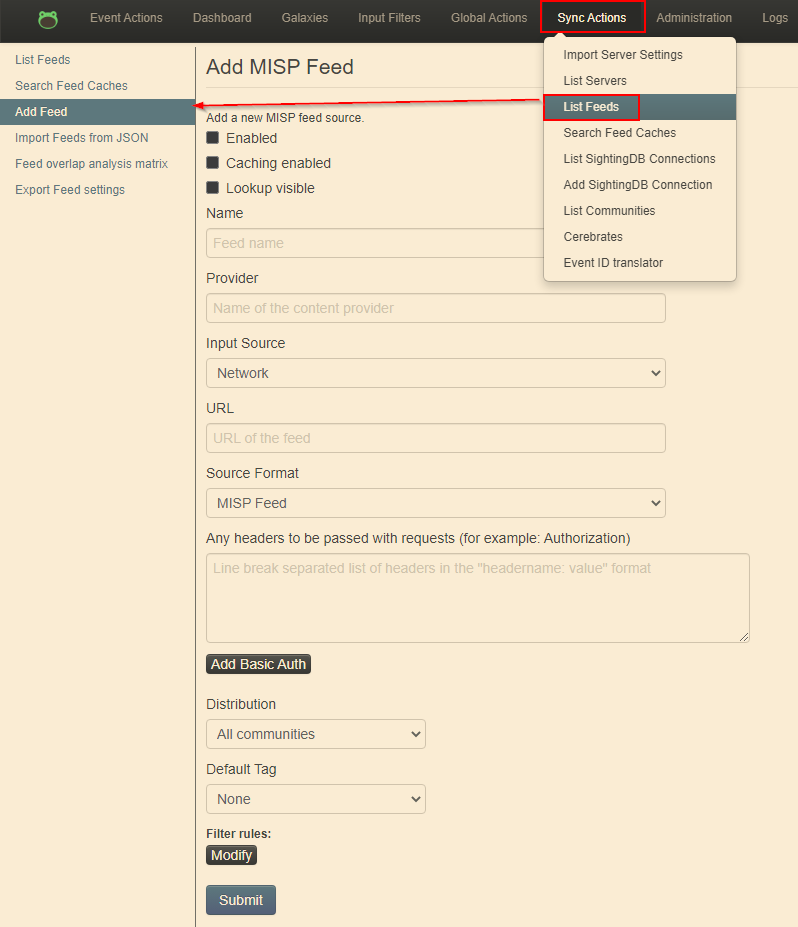
Now, we just need to add our configuration details to the new feed. Feel free to fill it out however you like but I’ll provide a template below:
Enabled = Y
Caching enabled = Y
Lookup visible = Y
Name = "Greynoise: Exploiting Confluence Hardcoded Credentials"
Provider = "Greynoise"
Input Source = "Network"
URL = "https://api.greynoise.io/v3/tags/18ac439f-c0b6-4d98-afcf-24de74d9b169/ips?format=txt&token=<unique key>"
Source Format = "Freetext Parsed Feed"
Creator organisation = "<Select your default MISP org>"
Target Event = "Fixed Event"
Target Event ID = <Leave Blank>
Auto Publish = Y
Delta Merse = Y
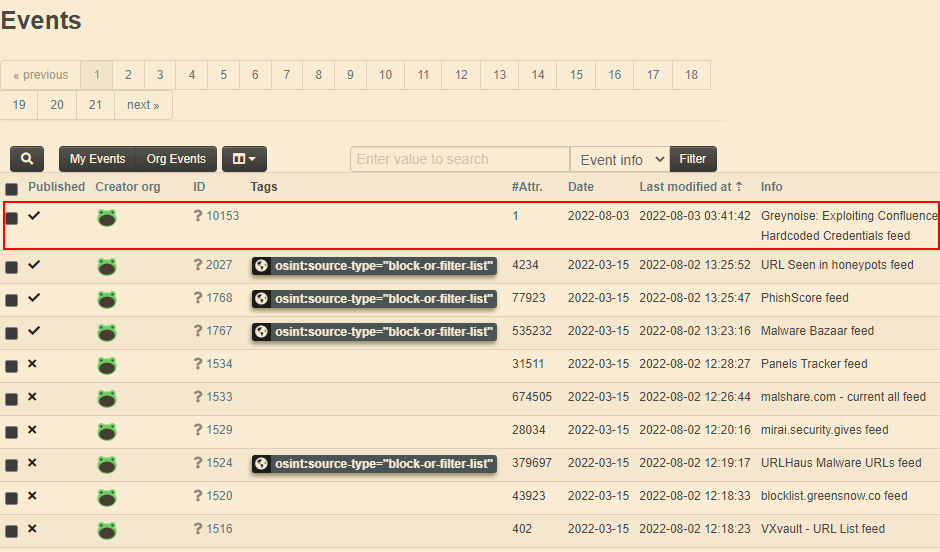
Once you’re happy with the feed configuration, now we will want to cache the feed; this will initiate a pull for all IoCs from our blocklist and also create the event where all of this data will live in MISP.

Give it a minute and you should see the new event is created and slowly populating with IoCs! Assuming you have automation set up on the MISP server, this event will be refreshed regularly.
TL;DR⌗
- Find a tag on GreyNoise you are interested in.
- Get unique URL blocklist from the Trends page corresponding to the tag you’ve chosen.
- Configure a new free-text feed in MISP using the URL you retrieved before.
- Cache feed for initial pull (or wait for your automation).