Malware Analysis Tips: Analyzing an Emotet Maldoc
Overview⌗
I came across a new Emotet campaign at work that was inevitably caught by our mail filter, but thought this was a good opportunity to learn more about extracting IoCs from these maldocs.
The Sample⌗
| Attribute | Value |
|---|---|
| SHA1 | 814b9961fbb5a75a00ca05591ac5a60d503bea22 |
| Filename | INFO_405261.xlsm |
| Sender | mark.amarilla@abbraza[.]com.ph |
| Date Received | March 14th, 2022 |
Analysis⌗
Upon opening the Excel document, you see a familiar banner urging users to allow macros - the banner is actually a static photo seen below by the context menu options.
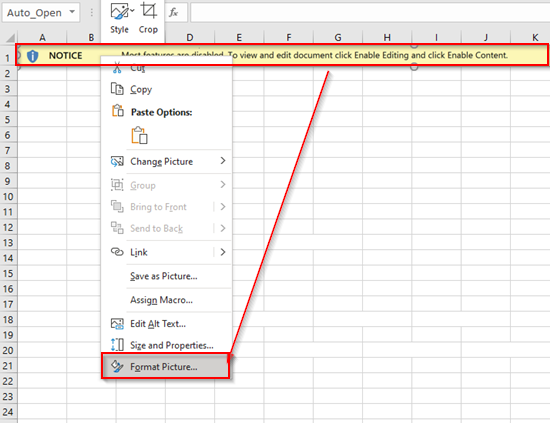
Now something is a little fishy with this document, the gridlines look off - select a cell and you unveil some hidden text.
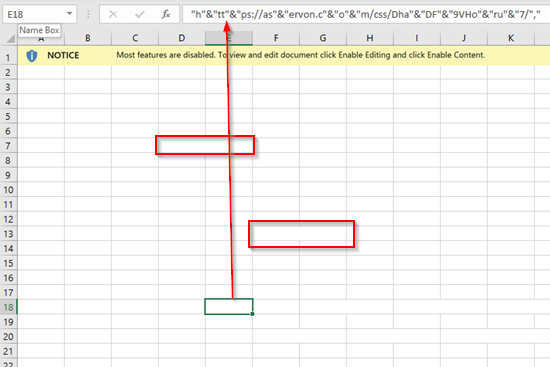
Next, you’ll want to grab all of these strings easily - use a simple trick to extract them from the maldoc; change the extension to .zip, unzip the maldoc and cat the shared strings table for some quick Cyber-Cheffin’.
cp INFO_405261.xlsm zipped.zip
unzip -d unzipped/ zipped.zip
cat unzipped/xl/sharedStrings.xml
Copy the file from stdout and paste into Cyber Chef so we can quickly replace unwanted characters - this could easily be done with sed or tr as well.
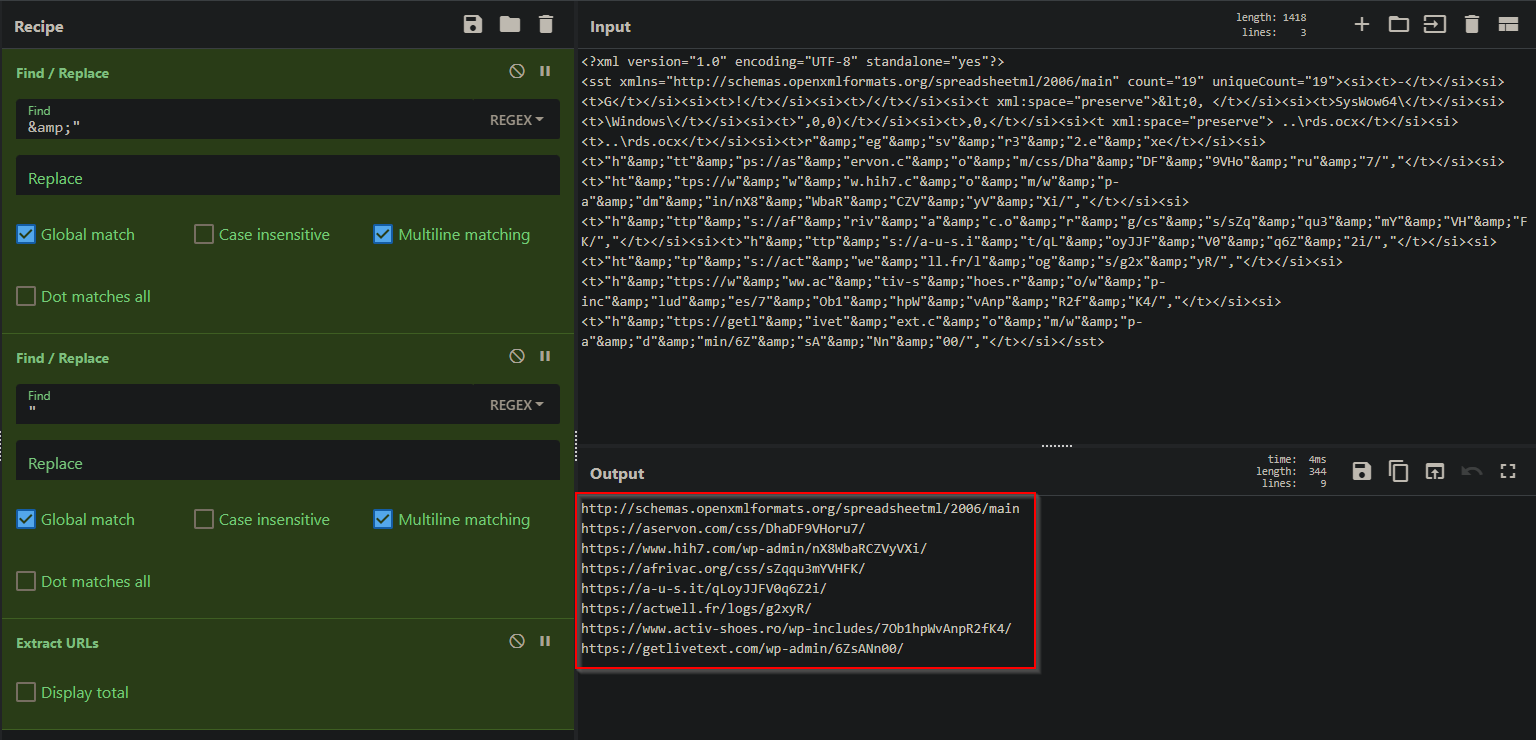
Now enjoy the fresh IoCs!
Conclusion⌗
Hopefully learned a quick trick to extract strings and manually grab IoCs from an Excel file without even needing Excel to do so!
I didn’t even begin to go into analyzing the actual maldoc execution chain and seeing what else it tries to load and possibly drop onto disk - all which of course leads to more IoCs! I leave that up to the audience.
Technical Appendix⌗
Table of IoCs
| Type | Value |
|---|---|
| SHA1 | 814b9961fbb5a75a00ca05591ac5a60d503bea22 |
| Filename | INFO_405261.xlsm |
| URL | hxxp://schemas[.]openxmlformats[.]org/spreadsheetml/2006/main |
| URL | hxxps://aservon[.]com/css/DhaDF9VHoru7/ |
| URL | hxxps://www[.]hih7[.]com/wp-admin/nX8WbaRCZVyVXi/ |
| URL | hxxps://afrivac[.]org/css/sZqqu3mYVHFK/ |
| URL | hxxps://a-u-s[.]it/qLoyJJFV0q6Z2i/ |
| URL | hxxps://actwell[.]fr/logs/g2xyR/ |
| URL | hxxps://www[.]activ-shoes[.]ro/wp-includes/7Ob1hpWvAnpR2fK4/ |
| URL | hxxps://getlivetext[.]com/wp-admin/6ZsANn00/ |