How to Write a Script
Greetings! Today I will be sharing my general script writing process and how they can improve your workflow. Below is the script I created which I’ll be using to go over how I approach creating scripts to help my pentesting workflow.
#!/bin/bash
# AutoEnum by Droogy
#
# AutoEnum is a simple service scanner built around nmap
#
printf 'gimme target: '
read target
nmap -p- -T4 $target -oN portscan
# read portscan file output and turn into CSV formatted ports for nmap
cat portscan | grep open | cut -d '/' -f 1 | \
tr '\n' , > ports.txt
# read file into variable
ports=$(<ports.txt)
# script categories
# auth, broadcast, brute, default. discovery, dos, exploit
# external, fuzzer, intrusive, malware, safe, version, and vuln
# should prob throw in UDP at some point
# -sU -top-ports 250
# finalized nmap scan to run against discovered ports
nmap -A -v -p$ports --script=discovery,vuln,brute\
--version-all $target -oN initial.log
clear
cat initial.log | grep tcp
So this script was developed while I was pursuing the eJPT certification and doing a lot of TryHackMe/VulnHub/HackTheBox/Hera boxes which naturally involves a TON of scanning and enumeration. This gets quite repetitive so I developed a script to make this process a bit easier.
I chose Bash as the language because it’s simple, readable, and super portable across Linux distros. I’m barely a competent programmer so if I can get an Nmap parser done in less than ten lines of bash imagine what you could do!
To begin with, we need to clearly define our problem, which makes coding much easier as we can break up our large problem into smaller ones. Some people like to use pseudo-code, but honestly any sort of pre-planning for a program/script works. The problem I need to solve can roughly be broken up into the following steps:
- I need a full portscan on a target
- parse those ports into a variable/file
- Format them in a way that works with nmap
- feed the ports back into nmap and re-enumerate the discovered ports, this time with script/service scanning
Let’s break the code into chunks and take a look at what each one does.
printf 'gimme target: '
read target
nmap -p- -T4 $target -oN portscan
This is pretty self explanatory, the script prompts the user for input, reads that into a variable and then runs a full portscan against that target and saves output into a file called “portscan”.
cat portscan | grep open | cut -d '/' -f 1 | \
tr '\n' , > ports.txt
Next up is an ugly little bit which formats our portscan results into a CSV formatted list of ports which we will need to feed back into Nmap in our next step. Let’s break up the code further and see what each bit does.
cat portscan– reads the portscan resultsgrep open– searches for the word “open”, which would be on the same line as the port we need to grabcut -d '/' -f 1– separates strings by the delimiter which is ‘/’ in our case and then the -f switch selects the first field, which is the port itself with no extra texttr '\n' , > ports.txt– finally, the translate (tr) command replaces all new lines with commas – thus creating a list of CSV formatted ports which can be fed into Nmap!
To conclude, the above chunk of code turns a file this
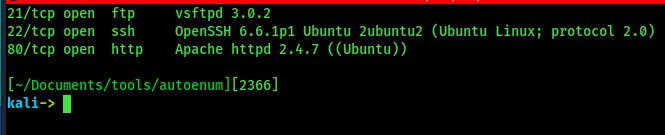
Into this: 21,22,80
Next, since Nmap doesn’t exactly allow for reading a file with a list of ports, we will export the previous CSV list of ports into a variable with this neat bash trick.
ports=$(<ports.txt)
Finally, the last part is pretty self-explanatory, we start a comprehensive Nmap scan utilizing the open ports we found and then output these results to the terminal as show below.
nmap -A -v -p$ports --script=discovery,vuln,brute \
--version-all $target -oN initial.log ;
clear;
cat initial.log | grep tcp;
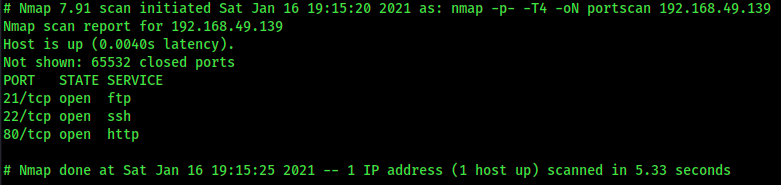 final output
final output