Creating a Windows Defender Rule for Spotify Connect Traffic
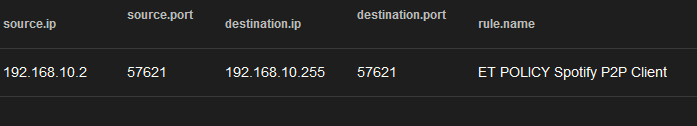
Quick post today about cleaning up your network traffic and nipping unnecessary broadcast traffic in the bud. I look at my Security Onion logs maybe once a day when I have time and I couldn’t help but always notice this particular log showing Spotify sending packets to broadcast quite often.
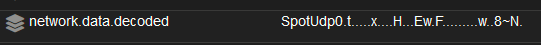
Taking a further look at the logs, I can see the packet data decoded which confirms this is Spotify sending UDP packets from my host to broadcast.
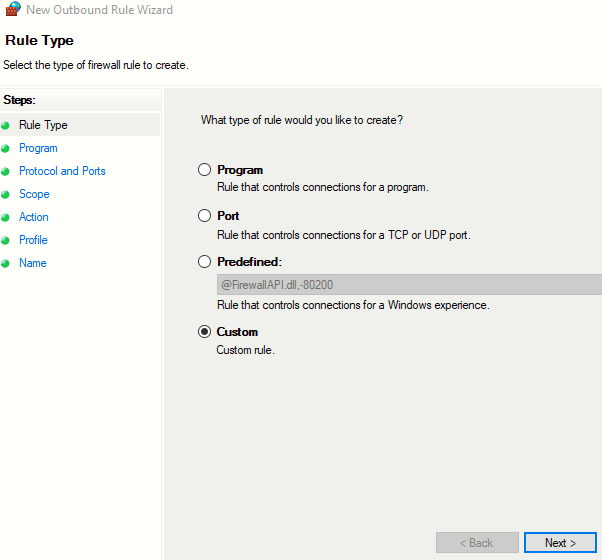
Now the Spotify Connect protocol is pretty cool and allow inter-connectivity between devices both running Spotify. Meaning I can play and control my song selection on my phone via my PC and vice versa. But is this something I need? Nope. So let’s create a quick Defender Firewall rule to block this functionality and clean up my Security Onion logs. First we are going to bring up the Firewall MMC snap-in and create a new Custom Outbound Rule.
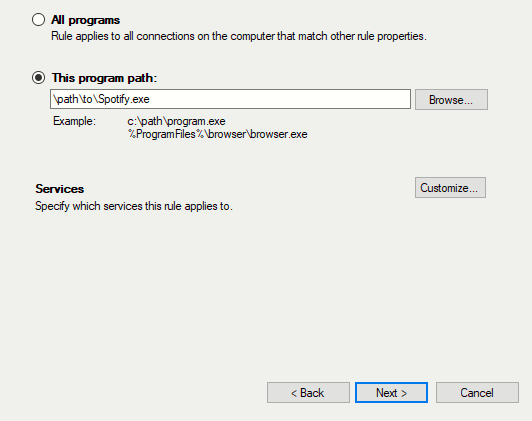
Spotify has a weird default service path inside the User\AppData folder so hunt Spotify.exe down and add it to our rule.
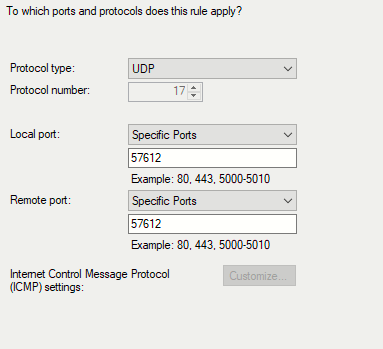
In my case, the ephemeral port was 57612 for both local and remote port. Given the transient nature of ephemeral ports this could change but a quick Google search shows that this port is standard for Spotify Connect. So, we know that the protocol type is UDP and the port is 57612 – let’s further improve the rule on the next screen.
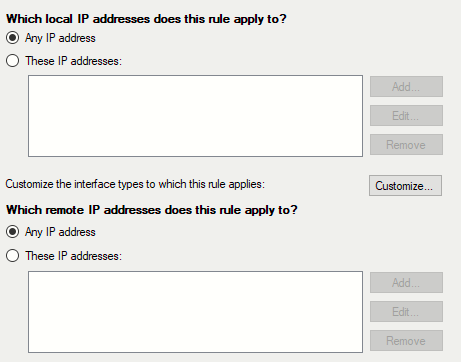
On the next prompt we can define the scope – this host is inside VLAN10 so I left the default ‘Any IP address’ since I don’t have to worry about other hosts on the subnet. Adjust accordingly for your own network.
On the next screen, we are going to naturally block this unwanted connection.

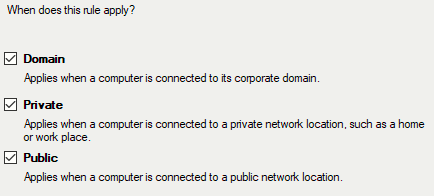
Next we’re going to apply this rule to all profiles, mileage may vary depending on any given person’s needs/usage.
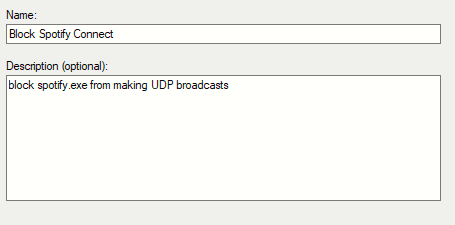
Finally, we just name the sucker and let it rip!
Looking at my Security Onion logs, they are now just a little bit cleaner and I don’t have to weed through those broadcast alerts anymore!